Cryptocurrency - Why is it safe and how does it work?

What makes cryptocurrency different from traditional money? What it boils down to: cryptocurrency requires trust in certain algorithms rather than in a central authority, like banks. But why would we want to use this and are these algorithms really that safe?
Decentralization
One of the main ways in which crypto differs from banks is that the ledger (the list of account balances) is not recorded at the headquarters of a bank, but everyone stores a copy. In addition, every transaction is broadcasted, so anyone can verify it.
Wait, but how can everyone store a copy of everyone’s balances, and should transactions not be hidden from everyone to see? The way in which the blockchain is designed to be decentralized will be discussed later in this article, but let us first look at one of the key building blocks of cryptocurrency: hash functions.
Hash functions
A basic refresher: how do hash functions work again and how are they made safe?
Firstly, take the following functions:
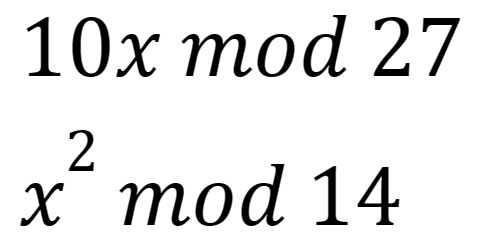
These are examples of functions that follow three of the requirements of a hash function H(x):
- It has a fixed-length output.
- H(x) is relatively simple to calculate for any given x.
- The output is deterministic, meaning that each time you calculate H(x) with the same x, the same output is recorded.
However, this is not enough. Another key property of hash functions is that, given some y, it is hard to find an x such that H(x)=y. This is called collision-resistance. In real life, hash functions are preferably built so that it would take millions of years to crack them, that is, find a collision. That is what constitutes their safety. So how do we make hash functions that are good, or ‘collision-resistant’?
Collision-resistance
Making cryptographic hash functions is something that experts experiment with a lot. The key features that lead to good hash function security are:
- The output appears completely unrelated to the input;
- Changing one bit of the input can completely change the output;
- The hash function must be hard to invert.
If that last requirement is not met, one can relatively easily find an x that collides with the target, that is, produces the same hash output. For example, take hash function the following parameters:
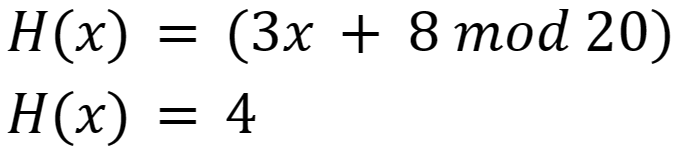
Then:
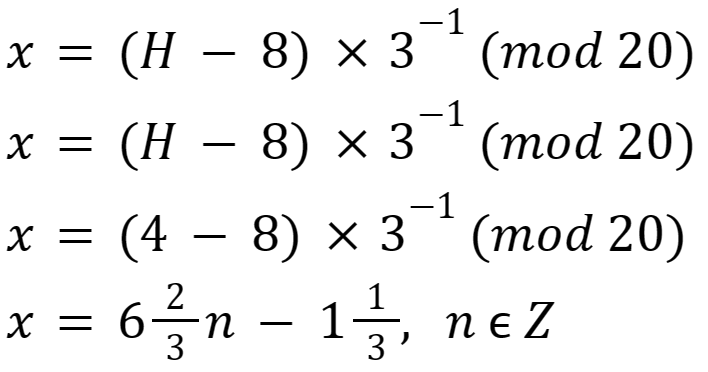
Any of these values of x will produce hash output 4.
Long story short: hash functions that consist of merely sequences of arithmetic operations (adding, subtracting, multiplying) can be inverted relatively easily by doing the same sequence of inverse operations. So what do we do to make our hash functions hard to invert?
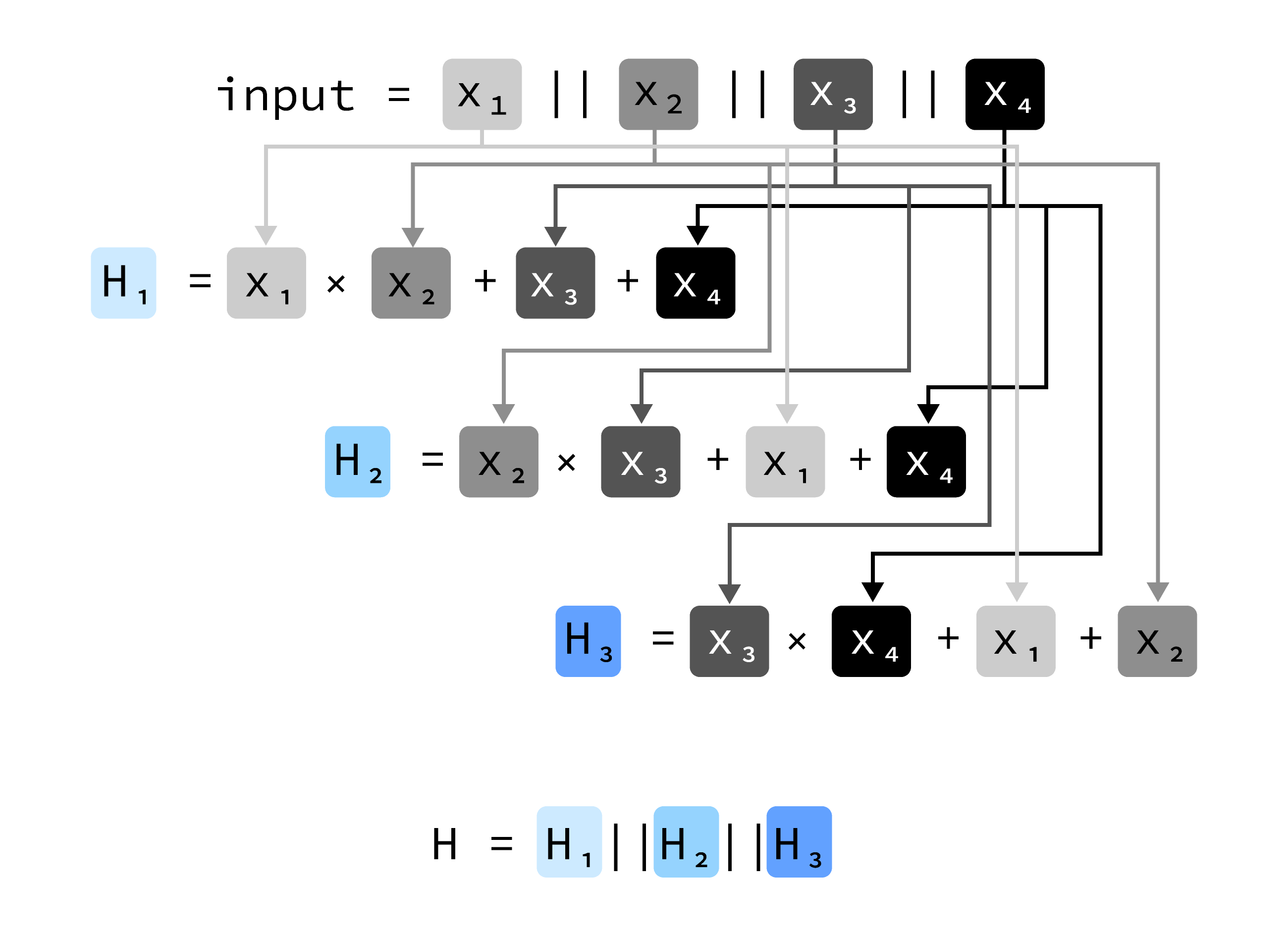
Layers upon layers-resistance
Consider the example hash function H in Figure 1:
Let us fill in this function and see what happens to the output:
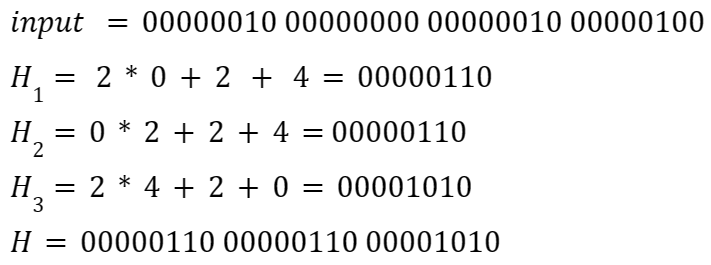
Now suppose an attacker who knows the algorithm would like to find a collision (an input that hashes to the final H), and makes the following random guess:
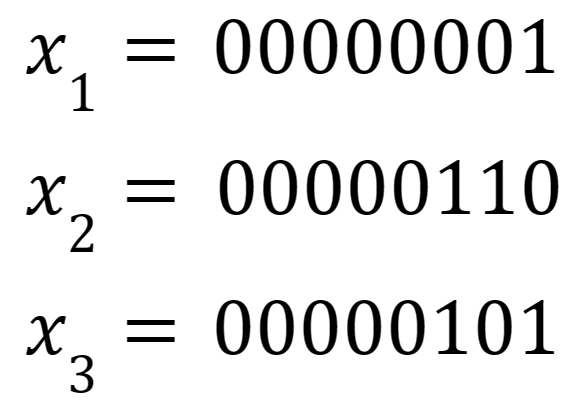
And then calculates x4 by:
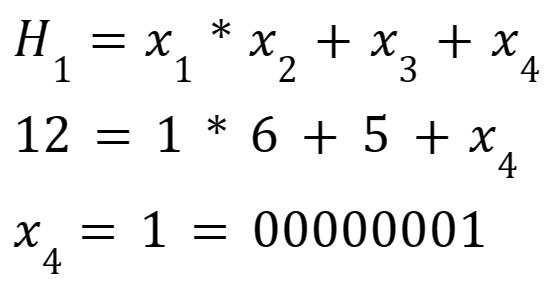
However, this combination of values will not produce the correct result:
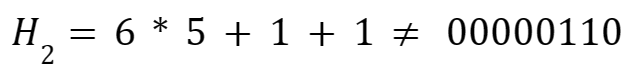
Therefore, the attacker has to guess H2. The same holds for H3. So the chance that both are correct is (approximately) 1/(2^16) (given a length 8 bits for both). This is a step in the way of collision-resistance, since the attacker now has no better strategy to find a collision than guessing. However, we may want to add other operations than just mod, such as the following:
- register shifts
- bitwise logic operations (OR, XOR, NOT, etc.)
Through layering of different types of operations, increasing the length of the hash output and adding more rounds of operations, our hash function can start to be harder and harder to find a collision for, getting closer and closer to a complete, mingled randomness, which is exactly what real hashing functions achieve with a lot of layers of operations and rounds.
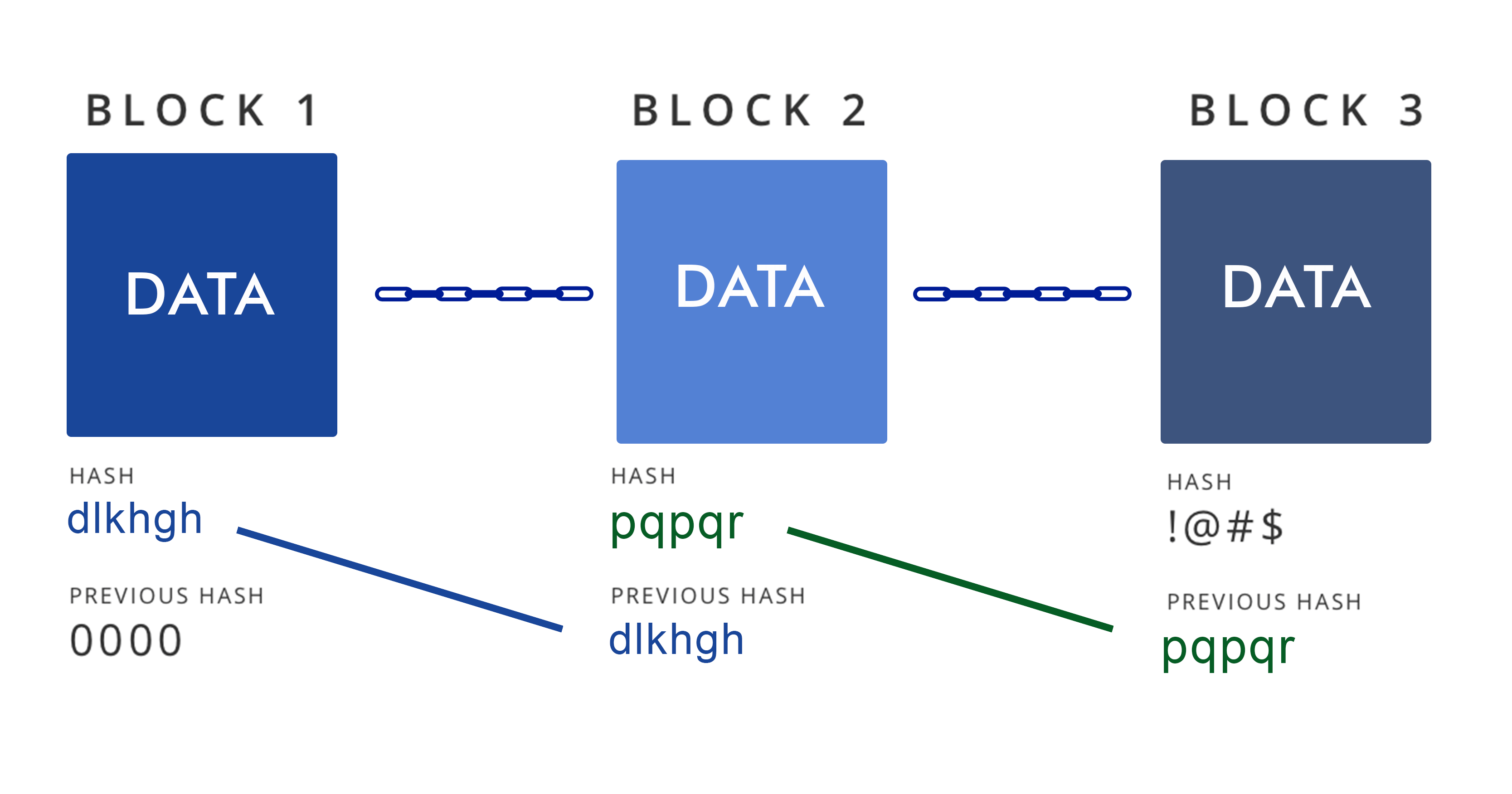
The blockchain
One of the key ideas in the data structure of the blockchain is the use of hash pointers: hashes that point to a block of information. These are useful so that we can find out if the actual block of information is in some way tampered with. Because every block contains a hash of the previous block, the blocks are said to be linked in a chain. If any item in the chain is changed, the changes in the hashes of the next blocks will propagate through the chain.
The future of cryptocurrency
Now that we have established the basics of cryptocurrency, you may think: “If cryptocurrency were to replace central authorities in the future, what would change?”. Firstly, the operation of the system would no longer be merely the responsibility of a central authority, but of all participants. There would be networks of thousands of people maintaining a copy of the blockchain on their computer. In addition, people would need to be able to participate on a smartphone, so participating should not impose unreasonable storage and computation requirements.
Such requirements and many more are already functionalities of many digital currencies today, and will be improved upon in the years to come, where emphasis will be placed on security. Although it is hard to predict where the technology will take the world, cryptocurrency is headed to have a fundamental impact on the way money is globally stored and spent.